Details
This Trojan provides a remote malicious user with access to the victim machine. It is a Windows PE EXE file. It is 48640 bytes in size. It is packed using UPX. The unpacked file is approximately 360KB in size.
Installation
The Trojan extracts the following file from its body:
%System%\aspimgr.exe
This file is 73728 bytes in size. Kaspersky Anti-Virus does not detect this file as malicious.
The original file will then be deleted.
The backdoor creates a service called "Microsoft ASPI Manager" which ensures the backdoor executable file will be launched each time the victim machine is restarted.
The Trojan launches a HTTP proxy server on the victim machine on TCP port 80. It then sends notification that the victim machine has been infected to the addresses shown below:
66.199.241.98
82.103.140.75
203.117.175.124
72.21.63.114
66.232.102.169
66.96.196.53
It does this by sending HTTP requests. Once infected, the victim machine becomes part of a zombie network and can be used to send spam or to conduct DoS attacks.
The backdoor creates the following log files:
%WinDir%\ws386.ini
%WinDir%\db32.txt
%WinDir%\s32.txt
%WinDir%\f32.txt
It creates the following registry key:
[HKLM\SOFTWARE\Microsoft\Sft]
and saves its configuration to this key.
Removal Guide
If your computer does not have an up-to-date antivirus, or does not have an antivirus solution at all, follow the instructions below to delete the malicious program:
1. Use Task Manager to terminate the malicious process
2. Delete the following registry key:
[HKLM\SOFTWARE\Microsoft\Sft]
3. Delete the "Microsoft ASPI Manager" service.
4. Delete the following files:
%WinDir%\ws386.ini
%WinDir%\db32.txt
%WinDir%\s32.txt
%WinDir%\f32.txt
%System%\aspimgr.exe
Tips about How to Choose Computer
Check Out
http://choosingcomputer.blogspot.com
Wednesday, August 27, 2008
Trojan.Win32.Agent.dcc
Once launched, the Trojan copies its executable file as shown below:
%System%\drivers\runtime.sys
In order to ensure that the Trojan is launched each time the system is started, it creates a system service called "Runtime" which launches the Trojan executable file each time Windows is booted. The following registry key will be created:
[HKLM\System\CurrentControlSet\Services\runtime]
Once installed, the Trojan deletes its original file.
This Trojan has a malicious payload. It is a Windows PE EXE file. It is 20480 bytes in size.
The Trojan contains a rootkit driver which masks the presence of Trojan files on the hard disk, and also the presence of the files listed below:
%System%\ntoskrnl.exe
%System%\ntkrnlpa.exe
%System%\ntkrnlmp.exe
%System%\ntkrpamp.exe
It also masks the presence of processes related to these files.
The Trojan also launches a hidden process called "iexplore.exe". It injects its code into this process, which will then download files from the following addresses:
208.66.194.***
66.246.252.***
208.66.195.***
74.53.42.***
74.53.42.***
Downloaded files will be saved as:
%TEMP%\.exe
with standing for a random sequence of numbers.
Once downloaded, the files will be launched for execution.
Removal Guide
If your computer does not have an up-to-date antivirus, or does not have an antivirus solution at all, follow the instructions below to delete the malicious program:
1. Use Task Manager to terminate the malicious program’s process.
2. Delete the following system registry key:
[HKLM\System\CurrentControlSet\Services\runtime]
3. Delete the following file:
%System%\drivers\runtime.sys
4. Delete the contents of %Temp%
Tips about How to Choose Computer
Check Out
http://choosingcomputer.blogspot.com
%System%\drivers\runtime.sys
In order to ensure that the Trojan is launched each time the system is started, it creates a system service called "Runtime" which launches the Trojan executable file each time Windows is booted. The following registry key will be created:
[HKLM\System\CurrentControlSet\Services\runtime]
Once installed, the Trojan deletes its original file.
This Trojan has a malicious payload. It is a Windows PE EXE file. It is 20480 bytes in size.
The Trojan contains a rootkit driver which masks the presence of Trojan files on the hard disk, and also the presence of the files listed below:
%System%\ntoskrnl.exe
%System%\ntkrnlpa.exe
%System%\ntkrnlmp.exe
%System%\ntkrpamp.exe
It also masks the presence of processes related to these files.
The Trojan also launches a hidden process called "iexplore.exe". It injects its code into this process, which will then download files from the following addresses:
208.66.194.***
66.246.252.***
208.66.195.***
74.53.42.***
74.53.42.***
Downloaded files will be saved as:
%TEMP%\
with
Once downloaded, the files will be launched for execution.
Removal Guide
If your computer does not have an up-to-date antivirus, or does not have an antivirus solution at all, follow the instructions below to delete the malicious program:
1. Use Task Manager to terminate the malicious program’s process.
2. Delete the following system registry key:
[HKLM\System\CurrentControlSet\Services\runtime]
3. Delete the following file:
%System%\drivers\runtime.sys
4. Delete the contents of %Temp%
Tips about How to Choose Computer
Check Out
http://choosingcomputer.blogspot.com
Tuesday, August 26, 2008
DriveGuard.exe Or FlashGuard.exe Virus
This virus also known as Worm.Win32.Autoit.au - kaspersky, this worm tries to impersonate a friendly application one that wants to protect your removable drives from other pieces of malware.
It also includes a readme file that reads:
"This tiny software is used to protect removable storage devices from
worms that are spread from one PC to another. "
But at the same time it will download backdoor files..
You can locate the virus at c:\Program Files\FlashGuard\FlashGuard.exe only if you unhide hidden files already(How to Unhide Hidden Files Guide)

The malicious file would copy itself to :
c:\Program Files\FlashGuard\FlashGuard.exe
c:\Program Files\FlashGuard\ReadMe.txt
c:\DocumentsandSettings\**UserProfile\LocalSettings\Temp\DriveGuard.tmp.exe
c:\DocumentsandSettings\**UserProfile\LocalSettings\Temp\gHmpg.tmp.exe
It create folders in your pendrive & copy itself to :
f:\System\Security\DriveGuard.exe *
f:\autorun.ini *
*[f:\] drive letter could vary depend on how Windows assign/mount your pendrive
Create startup launcher(Registry) :
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\FlashGuard
To see these virus you must set Windows to show hidden files - Guide
Removal Guide :
Press Ctrl+Alt+Del to open 'Task Manager', select FlashGuard.exe & click 'End Process'

You can browse to the folder mentioned above or you can find it quickly by using 'Search' feature(Start Menu>>Search). In the search box type, flashguard.exe or flashguard. Don't hit the search button yet..
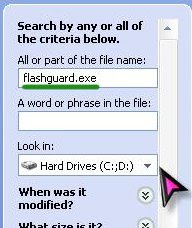
Scroll down & expand 'More Advanced Options'.Check the all the box as you see in the screenshot below & hit 'Search' button..
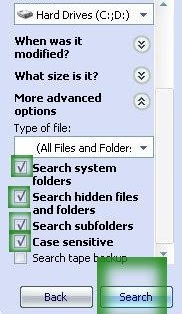
Delete all the files found..
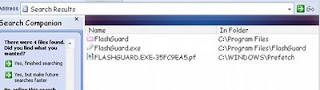
Also serch for .tmp.exe, delete DriveGuard.tmp.exe & gHmpg.tmp.exe files found..
The virus files can easily recognized with pendrive like icon..
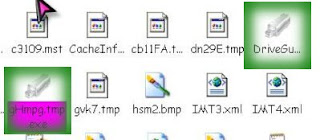
Your pc now clean from the virus, since the virus load at startup, it left an entry in your registry, you can delete it in registry or you can go to Start Menu>>Run, type msconfig & click 'Ok'.
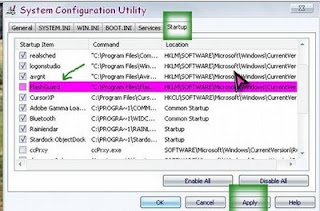
Select 'Startup' tab, select & uncheck FlashGuard. Click 'Apply' to take effect..
Delete Registry Entry : Go to Start Menu>>Run, type regedit & click 'Ok'
Browse to :
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\FlashGuard
Select FlashGuard, right-click on it & delete..
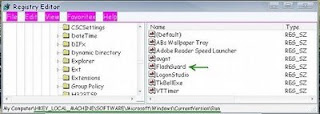
FlashGuard.exe cleaned..
If you new on manually on removing virus, this guide also useful for other type of virus too, especially the type that infecting removable drive(pendrive/flashdrive/memory card). It also depend on how strong the viruses, some viruses replicate itself with random/different file name(hard to find). As you can see FlashGuard.exe replicate itself as DriveGuard.tmp.exe & gHmpg.tmp.exe.

It also includes a readme file that reads:
"This tiny software is used to protect removable storage devices from
worms that are spread from one PC to another. "
But at the same time it will download backdoor files..
You can locate the virus at c:\Program Files\FlashGuard\FlashGuard.exe only if you unhide hidden files already(How to Unhide Hidden Files Guide)

The malicious file would copy itself to :
c:\Program Files\FlashGuard\FlashGuard.exe
c:\Program Files\FlashGuard\ReadMe.txt
c:\DocumentsandSettings\**UserProfile\LocalSettings\Temp\DriveGuard.tmp.exe
c:\DocumentsandSettings\**UserProfile\LocalSettings\Temp\gHmpg.tmp.exe
It create folders in your pendrive & copy itself to :
f:\System\Security\DriveGuard.exe *
f:\autorun.ini *
*[f:\] drive letter could vary depend on how Windows assign/mount your pendrive
Create startup launcher(Registry) :
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\FlashGuard
To see these virus you must set Windows to show hidden files - Guide
Removal Guide :
Press Ctrl+Alt+Del to open 'Task Manager', select FlashGuard.exe & click 'End Process'

You can browse to the folder mentioned above or you can find it quickly by using 'Search' feature(Start Menu>>Search). In the search box type, flashguard.exe or flashguard. Don't hit the search button yet..

Scroll down & expand 'More Advanced Options'.Check the all the box as you see in the screenshot below & hit 'Search' button..

Delete all the files found..

Also serch for .tmp.exe, delete DriveGuard.tmp.exe & gHmpg.tmp.exe files found..

The virus files can easily recognized with pendrive like icon..

Your pc now clean from the virus, since the virus load at startup, it left an entry in your registry, you can delete it in registry or you can go to Start Menu>>Run, type msconfig & click 'Ok'.

Select 'Startup' tab, select & uncheck FlashGuard. Click 'Apply' to take effect..
Delete Registry Entry : Go to Start Menu>>Run, type regedit & click 'Ok'
Browse to :
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\FlashGuard
Select FlashGuard, right-click on it & delete..

FlashGuard.exe cleaned..
If you new on manually on removing virus, this guide also useful for other type of virus too, especially the type that infecting removable drive(pendrive/flashdrive/memory card). It also depend on how strong the viruses, some viruses replicate itself with random/different file name(hard to find). As you can see FlashGuard.exe replicate itself as DriveGuard.tmp.exe & gHmpg.tmp.exe.

system.exe backdoor spyware
System.exe is a Backdoor W32.Spybot.OBB.
System.exe spreads by e-mail and via network shares.
System.exe monitors user Internet activity and private information.
It sends stolen data to a hacker site
Related files :
"c:\Windows\system.exe" or "c:\Windows\system32\system.exe"
Solution :
1. update your antivirus and scan it ... ehehehe
2. Manual Removal
MANUAL REMOVAL
Step 1: Use Windows File Search Tool to Find system.exe Path
1. Go to Start > Search > All Files or Folders.
2. In the "All or part of the the file name" section, type in " system.exe" file name(s).
3. To get better results, select "Look in: Local Hard Drives" or "Look in: My Computer" and then click "Search" button.
4. When Windows finishes your search, hover over the "In Folder" of " system.exe", highlight the file and copy/paste the path into the address bar. Save the file's path on your clipboard because you'll need the file path to delete system.exe in the following manual removal steps.
Step 2: Use Windows Task Manager to Remove system.exe Processes
1. To open the Windows Task Manager, use the combination of CTRL+ALT+DEL or CTRL+SHIFT+ESC.
2. Click on the "Image Name" button to search for " system.exe" process by name.
3. Select the " system.exe" process and click on the "End Process" button to kill it.
Step 3: Detect and Delete Other system.exe Files
1. To open the Windows Command Prompt, go to Start > Run > cmd and then press the "OK" button.
2. Type in "dir /A name_of_the_folder" (for example, C:\Spyware-folder), which will display the folder's content even the hidden files.
3. To change directory, type in "cd name_of_the_folder".
4. Once you have the file you're looking for type in del "name_of_the_file".
5. To delete a file in folder, type in "del name_of_the_file".
6. To delete the entire folder, type in "rmdir /S name_of_the_folder".
7. Select the " system.exe" process and click on the "End Process" button to kill it.
Tips About Choosing Your Computer
Check Out
http://choosingcomputer.blogspot.com
System.exe spreads by e-mail and via network shares.
System.exe monitors user Internet activity and private information.
It sends stolen data to a hacker site
Related files :
"c:\Windows\system.exe" or "c:\Windows\system32\system.exe"
Solution :
1. update your antivirus and scan it ... ehehehe
2. Manual Removal
MANUAL REMOVAL
Step 1: Use Windows File Search Tool to Find system.exe Path
1. Go to Start > Search > All Files or Folders.
2. In the "All or part of the the file name" section, type in " system.exe" file name(s).
3. To get better results, select "Look in: Local Hard Drives" or "Look in: My Computer" and then click "Search" button.
4. When Windows finishes your search, hover over the "In Folder" of " system.exe", highlight the file and copy/paste the path into the address bar. Save the file's path on your clipboard because you'll need the file path to delete system.exe in the following manual removal steps.
Step 2: Use Windows Task Manager to Remove system.exe Processes
1. To open the Windows Task Manager, use the combination of CTRL+ALT+DEL or CTRL+SHIFT+ESC.
2. Click on the "Image Name" button to search for " system.exe" process by name.
3. Select the " system.exe" process and click on the "End Process" button to kill it.
Step 3: Detect and Delete Other system.exe Files
1. To open the Windows Command Prompt, go to Start > Run > cmd and then press the "OK" button.
2. Type in "dir /A name_of_the_folder" (for example, C:\Spyware-folder), which will display the folder's content even the hidden files.
3. To change directory, type in "cd name_of_the_folder".
4. Once you have the file you're looking for type in del "name_of_the_file".
5. To delete a file in folder, type in "del name_of_the_file".
6. To delete the entire folder, type in "rmdir /S name_of_the_folder".
7. Select the " system.exe" process and click on the "End Process" button to kill it.
Tips About Choosing Your Computer
Check Out
http://choosingcomputer.blogspot.com
Virus "81u3f4nt45y - 24.01.2007 - Surabaya”
Jika anda dipaparkan dengan message seperti dibawah setiap kali anda menghidupkan komputer anda bererti anda sudah terkena virus:
“Surabaya in my birthday
Don’t kill me, i’m just send message from your computer
Terima kasih telah menemaniku walaupun hanya sesaat, tapi bagiku sangat berarti
Maafkan jika kebahagiaan yang kuminta adalah teman sepanjang hidupku
Seharusnya aku mengerti bahwa keberadaanku bukanlah disisimu, hanyalah lamunan dalam sesal
Untuk kekasih yang tak kan pernah kumiliki 3r1k1m0″
Cara untuk membuang virus pesanan ini:
1.klik ke start-> run kemudian taip regedit dan enter.
2.Setelah program register editor muncul, sila klik urutan berikut pada window kiri :
“HKEY_LOCAL_MACHINE” -> “SOFTWARE” -> “Microsoft” -> “Windows NT” -> “Current Version” -> “WinLogon”.
dibahagian kanan window, delete item “LegalNoticeCaption” dan “LegalNoticeText”.
3. selesai
Tips About Choosing Your Computer
Check Out
http://choosingcomputer.blogspot.com
“Surabaya in my birthday
Don’t kill me, i’m just send message from your computer
Terima kasih telah menemaniku walaupun hanya sesaat, tapi bagiku sangat berarti
Maafkan jika kebahagiaan yang kuminta adalah teman sepanjang hidupku
Seharusnya aku mengerti bahwa keberadaanku bukanlah disisimu, hanyalah lamunan dalam sesal
Untuk kekasih yang tak kan pernah kumiliki 3r1k1m0″
Cara untuk membuang virus pesanan ini:
1.klik ke start-> run kemudian taip regedit dan enter.
2.Setelah program register editor muncul, sila klik urutan berikut pada window kiri :
“HKEY_LOCAL_MACHINE” -> “SOFTWARE” -> “Microsoft” -> “Windows NT” -> “Current Version” -> “WinLogon”.
dibahagian kanan window, delete item “LegalNoticeCaption” dan “LegalNoticeText”.
3. selesai
Tips About Choosing Your Computer
Check Out
http://choosingcomputer.blogspot.com
HOW TO REMOVE PC-OFF.BAT Trojan
1. Open "task manager" by pressing CTRL-ALT-DEL. Under tab 'processes', select 'password_viewer.exe' or 'bar311.exe' or 'photo.zip.exe' and Click ‘End Process’
2. Open "register editor"( click 'START’--> ‘RUN’ , type “regedit”) .
• GO TO ‘HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon’
FIND KEY
"Userinit" = C:\WINDOWS\system32\userinit.exe,bar311.exe"
----> remove value ‘bar311.exe’ ONLY!!!!
OR
"Userinit" = C:\WINDOWS\system32\userinit.exe,photo.zip.exe"
----> remove value ‘photo.zip.exe’ ONLY!!!!
OR
"Userinit" = C:\WINDOWS\system32\userinit.exe,password_viewer.exe"
----> remove value ‘password_viewer.exe’ ONLY!!!!
*/DO NOT REMOVE “USERINIT.EXE” VALUE OR “USERINIT” KEY, OR ELSE YOUR PC CANNOT ENTER YOUR WINDOWS/*
• GO TO ‘HKEY_CURRENT_USER \software\microsoft\windows\currentversion\explorer\advanced’
Change Value data for Key As Shown Below :-
"Hidden"=dword:00000001 (1) - Change to ‘1’
"HideFileExt"=Dword:00000000 (0) - Change to ‘0’
"ShowSupperHidden"=Dword:00000001 (1) – Change to ‘1’
• GO TO
‘HKEY_CURRENT_USER \software\microsoft\Command Processor’
FIND KEY
"autorun=c:\windows\pc-off.bat"
-----> Remove "c:\windows\pc-off.bat" or Delete autorun key
. go to ThumbDrive DRIVE(Do not doubleclick the drive,Use Address panel to view file inside DRIVE)
4. delete - autorun.inf
password_viewer.exe
bar311.exe
photo.zip.exe
5. Open Notepad and Type -
@echo off
del /a /f c:\windows\bar311.exe
del /a /f c:\windows\password_viewer.exe
del /a /f c:\windows\photo.zip.exe
del /a /f c:\windows\pc-off.bat
pause
6. Save As "remove.bat"
7. Run remove.bat
8. GO TO
C:\Windows\
Find bar311.exe OR password_viewer.exe OR photo.zip.exe OR pc-off.bat and delete it.
Tips About Choosing Your Computer
Check Out
http://choosingcomputer.blogspot.com
2. Open "register editor"( click 'START’--> ‘RUN’ , type “regedit”) .
• GO TO ‘HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon’
FIND KEY
"Userinit" = C:\WINDOWS\system32\userinit.exe,bar311.exe"
----> remove value ‘bar311.exe’ ONLY!!!!
OR
"Userinit" = C:\WINDOWS\system32\userinit.exe,photo.zip.exe"
----> remove value ‘photo.zip.exe’ ONLY!!!!
OR
"Userinit" = C:\WINDOWS\system32\userinit.exe,password_viewer.exe"
----> remove value ‘password_viewer.exe’ ONLY!!!!
*/DO NOT REMOVE “USERINIT.EXE” VALUE OR “USERINIT” KEY, OR ELSE YOUR PC CANNOT ENTER YOUR WINDOWS/*
• GO TO ‘HKEY_CURRENT_USER \software\microsoft\windows\currentversion\explorer\advanced’
Change Value data for Key As Shown Below :-
"Hidden"=dword:00000001 (1) - Change to ‘1’
"HideFileExt"=Dword:00000000 (0) - Change to ‘0’
"ShowSupperHidden"=Dword:00000001 (1) – Change to ‘1’
• GO TO
‘HKEY_CURRENT_USER \software\microsoft\Command Processor’
FIND KEY
"autorun=c:\windows\pc-off.bat"
-----> Remove "c:\windows\pc-off.bat" or Delete autorun key
. go to ThumbDrive DRIVE(Do not doubleclick the drive,Use Address panel to view file inside DRIVE)
4. delete - autorun.inf
password_viewer.exe
bar311.exe
photo.zip.exe
5. Open Notepad and Type -
@echo off
del /a /f c:\windows\bar311.exe
del /a /f c:\windows\password_viewer.exe
del /a /f c:\windows\photo.zip.exe
del /a /f c:\windows\pc-off.bat
pause
6. Save As "remove.bat"
7. Run remove.bat
8. GO TO
C:\Windows\
Find bar311.exe OR password_viewer.exe OR photo.zip.exe OR pc-off.bat and delete it.
Tips About Choosing Your Computer
Check Out
http://choosingcomputer.blogspot.com
Subscribe to:
Comments (Atom)