This Trojan has a malicious payload. It is a Windows dynamic link library (DLL) file. It is 361216 bytes in size.
Once launched, the program will display a message stating that the computer has been infected by malicious programs:
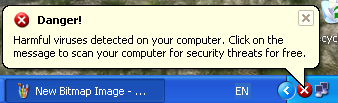
The message is displayed even if there are no other malicious programs on the computer.
If the user clicks the message, the program will display a license agreement in a new window:
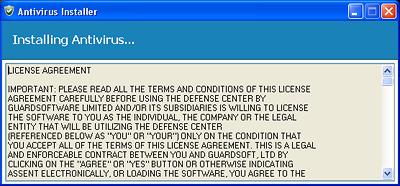
The program then starts to load a fake antivirus solution without waiting for the user’s consent:
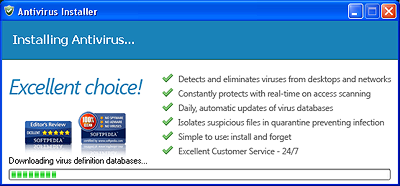
It is downloaded from one of the following addresses (depending on the file which contains the malicious program):
http://searchbad.org
http://searchfinddeliver.org
http://finderwid.org
http://searchannoying.org
http://fastoutostop.com
The following files are downloaded:
/avt/avt_db
/avt/avt_ext
/avt/avt_hook
/avt/avt_un
/avt/avt_main
The downloaded program is then installed into the directory:
%ProgramFiles%\AnVi
In order to ensure that it is launched automatically when the system is rebooted, the Trojan adds a link to the program which has just been installed to the system registry autorun key:
[HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
"Antivirus"="%ProgramFiles%\AnVi\avt.exe\ -noscan"
At the time of writing the following program could be downloaded and installed from the above addresses:
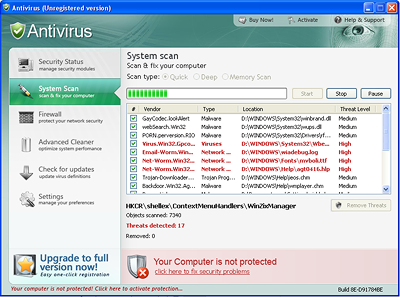
This program informs the user of the presence of various malicious programs in the system even if there are no such programs on the computer. In addition, it displays alerts about a network attack on the computer and the existence of a keylogger in the system:
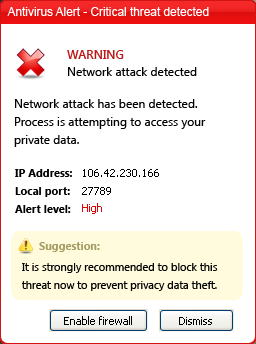
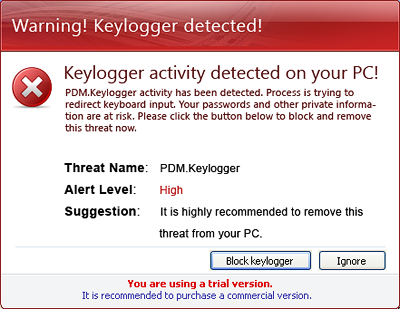
The program states that the full version has to be activated in order to remove these supposed “threats”. The user is prompted to make an electronic transaction using a bank card.
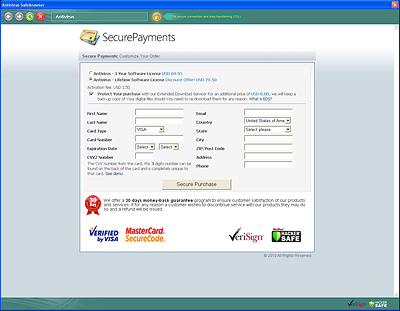
The program also prevents Windows Task Manager from being launched by modifying the following system registry key values:
[HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"DisableTaskMgr"=dword:00000001
[HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system]
"DisableTaskMgr"=dword:00000001
In addition, the malicious program creates the following system registry key:
[HKLM\SOFTWARE\AnVi]
Remove
If your computer does not have an up-to-date antivirus, or does not have an antivirus solution at all, follow the instructions below to delete the malicious program:
1. Delete the original malware file which is usually located in the
%TEMP%
folder named as
eapp32hst.dll
2. Enable the launch of Task Manager by restoring the following system registry key values:
3. [HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
4. "DisableTaskMgr"=dword:00000000
5. [HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system]
6. "DisableTaskMgr"=dword:00000000
7. Use Task Manager to terminate the process.
8. Delete the
%ProgramFiles%\AnVi
folder with all its contents.
9. Delete the following system registry key parameters:
10. [HKCU\Software\Microsoft\Windows\CurrentVersion\Run]
11. "Antivirus"="%ProgramFiles%\AnVi\avt.exe\ -noscan"
12. [HKLM\SOFTWARE\AnVi]
13. Delete all files from the %Temp% directory.